Most mid-size businesses don’t have the man power or budget to implement the necessary security controls. Often times they will have one or two IT people who is doing everything and is on a constant fire fighting mode.
Everyday there is a new threat and you are scrambling to patch it. Below are few important things that can keep mid-size companies a good baseline protection. If you are not doing these things you are a prime target for bad actors. Worse, your chances of recovery from an incident is less.
E-mail Security

What is the biggest open hole in your perimeter security? E-mail. Anyone can e-mail you a malicious attachment. The rogue players are getting more and more creative each day. They are spending time researching about you before sending you a malicious attachment. You like hockey, they will send you something about hockey, you like pets, they will send you a coupon for pet care. Even a careful person can fall prey to such e-mails. If you are not using a good e-mail security tool, it is guaranteed that someone in your company will click on it.
Invest In A Good Anti-virus, Anti-ransomware and EDR
Imagine, one of those malicious e-mails get past through your e-mail security. You want some form of defense to prevent it from causing damage throughout the company.
A good anti-virus/anti-ransom ware tool will help you with that. The default anti-virus that comes with your Windows laptop may not be sufficient to protect your device and data it holds.
Invest in a good anti-virus, anti-ransom product with EDR feature.
Use A Password Manager
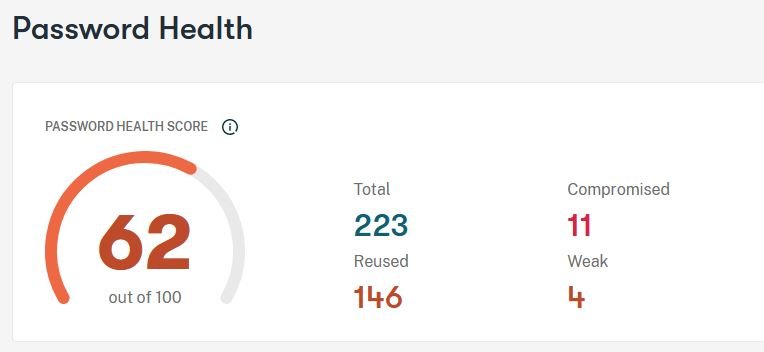
A password manager does way more than just protecting the password. It can automatically create complex passwords for you.
Your employee don’t have to deal with creating complex passwords. A password manager will tell you the strength of all the passwords in your vault. It also tells you how many times a password is reused.
A good password manager is absolutely worth the investment.
Implement 2FA
2FA is the first and most important line of defense for weak or compromised passwords.
2FA prevents hacking into your office365, G-suite, salesforce or any cloud application. If you do not use 2FA for your cloud applications, you are a prime target for bad actors.
Turn on Geo-Fencing for Cloud Applications
If you don’t have employees outside of United States, why allow access to e-mail from other countries?
Most of the breaches originate from a handful of countries. By disabling access to your data from these regions you can cut down the risk significantly.
It is not a perfect solution. Hackers can find a compromised device in an allowed region. But it takes an extra step.
Turning on geo-fencing for cloud applications adds another layer of security.
Test for Vulnerability
Remember that web server that you built for a new application, but you never used.
It is now sitting without a proper certificate and firewall ports open. No one can remember every device, application, ports and rules in their environment.
This is where a vulnerability testing will come into play. Performing a vulnerability testing will identify all the holes both inside and outside your system.
It will pin-point the vulnerabilities in every device in your organization so that you can fix it.
Patch Often
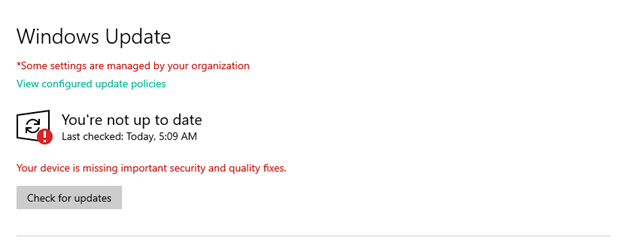
Patching is the single biggest contributor to security breaches.
Your vulnerability testing can give you details of what needs to be patched. But if you don’t patch in a timely manner, you are now more liable when a breach happens.
Backup and Restore

A good backup and restore is your insurance policy in case of a ransomware. A good backup will get you back on your feet in case the bad guys managed to encrypt your data. Please read the blog on why you want your back to be not a cloud only back at the link below.
E-mail and Productivity Suite Backup
Most people think your Office365 or G-suite is automatically backed up. In reality, you lose anything that is deleted after 30 days. It could be intentional or accident. 30 days may sound like a lot, but when you are busy running a business, it can go unnoticed for much longer time.
You can turn on litigation-hold as a short-term solution. But it is better to do a proper back up of your e-mails and file system.
These services are not super expensive and are quite affordable.
Encrypt Your Hard Disk
People lose laptops. But that doesn’t mean you need to lose the data along with it.
Encrypting your laptop hard disk protects your data from a lost laptop.
Summary
Securing your business is not easy in today’s world. New threats and vulnerabilities are showing up every day.
However, doing some of the basic protection can still reduce your attack surface significantly.
The list itself is not complete or comprehensive. But if you are not even doing this, you are a sitting duck for the bad actors.




