Index of Content
-
Introduction: The Security Game-Changer You Can’t Ignore
-
What’s SASE: Not Just Another Security Product
-
Why Does SASE Matter?
-
The Pressing Need For New Security Architecture
-
SASE: The Game-Changer You’ve Been Waiting For
-
The Insider’s Guide To Choose the Right SASE Vendor
-
Assess Where You Are Now Before You Act
-
Your Next Steps For Cybersecurity Excellence
-
Your Roadmap to Cybersecurity Excellence
Introduction: The Security Game-Changer You Can’t Ignore
Welcome to the frontlines of cybersecurity. If you’re an IT admin in a mid-sized U.S. company, you’re not just a cog in the machine; you’re the gatekeeper.
In a world where threats evolve faster than you can say “firewall,” staying ahead of the game is non-negotiable.
Enter SASE, or Secure Access Service Edge, your new secret weapon.
The Urgency of the Moment: Why You Should Read This Now
Let’s cut to the chase: Secure Access Service Edge (SASE), SD-WAN, FWaaS and Zero Trust Network Access (ZTNA) for Healthcare Explained are not mere industry jargon.
They’re the keys to fortifying your company’s digital fortress. Ignore them at your peril.
This guide is your playbook, your confidential dossier for navigating the complex world of cybersecurity in healthcare.
Why read this now? Because procrastination is the enemy #1 of security.
What to Expect from This Guide
In the sections ahead, we’ll dissect what Secure Access Service Edge (SASE) is and why it’s the linchpin of future healthcare security.
We’ll delve into its roots, its significance, and its practical applications. We’ll also guide you on how to choose the right vendor, so you’re not just secure; you’re strategically secure.
The Forrester Connection: Zero Trust Edge
But wait, there’s more. Ever heard of Zero Trust Edge (ZTE)?
Forrester, a leading market research company, coined this term, and it’s closely aligned with SASE. We’ll unpack this concept, so you’re not just riding the wave; you’re steering the ship.
Both frameworks, SASE and ZTE, advocate a “never trust, always verify” approach, emphasizing the need for stringent security protocols regardless of the user’s location or device.
What’s SASE: Not Just Another Security Product
Let’s clarify: Secure Access Service Edge (SASE) isn’t a plug-and-play gadget.
SASE is a revolutionary security architecture, conceptualized by Gartner. It’s designed to meet the dynamic demands of today’s digital landscape. Think of it as the blueprint you didn’t know you needed, but once you grasp it, you’ll question how you ever managed without it.
So, are you ready to transition from a rule-follower to a rule-maker in the IT realm? Buckle up.
This journey promises to be transformative.
Why Does SASE Matter?
In an era where remote work, cloud computing, and mobile access are the norm, traditional security measures often fall woefully short. SASE comes to the rescue by offering a more flexible, scalable, and secure solution.
SASE combines various security services like data loss prevention, firewall-as-a-service, and secure web gateways into a single, unified platform.
This not only simplifies the security stack but also enhances the organization’s ability to adapt to changing conditions swiftly.
The Pressing Need For New Security Architecture
Why the Need for a New Security Paradigm?
In recent years, businesses have undergone two seismic shifts that have fundamentally altered the security landscape: the migration of services to the cloud and the decentralization of the workforce. These aren’t mere trends; they’re the new normal. And they demand a new approach to security.
Reason 1: The Great Cloud Migration
Companies have increasingly transitioned their workloads to the cloud for a multitude of reasons, from cost-efficiency to scalability. Many new enterprises have even adopted a “cloud-first” approach, eschewing on-premise infrastructure altogether.
- The Upside of Migrating to the Cloud
On the bright side, this migration means fewer assets to protect within your physical office space. The need for an extensive on-premise firewall, data center, or even a VPN for remote employees has diminished.
- The Security Implications of Migration
However, the cloud migration also resembles the Wild West—lawless and unpredictable.The traditional security perimeter has dissolved. Employees can access company applications from anywhere, provided they have an internet connection.
For cybercriminals, this is a golden opportunity to exploit vulnerabilities from any location, undetected. Moreover, your security is only as strong as your cloud service provider.
Choose wisely, and you reap the benefits of robust security measures. Choose poorly, and you’re exposing your business to unnecessary risks.
Alarmingly, many companies are unaware of the full extent of their cloud application portfolio, as any employee with a company email and credit card can subscribe to new services, potentially jeopardizing data security.
Reason 2: The Remote Work Revolution
The COVID-19 pandemic has normalized remote work, making it a permanent fixture in the business landscape. Employees are now working from various locations—homes, coffee shops, or even other countries.
According to a Gartner survey, 82% of company leaders plan to allow employees to work remotely some of the time.
- The Security Conundrum Caused By Remote Working
Traditional VPN solutions are no longer viable; they create bottlenecks and lack granular control.
- The Perimeter is Dead.
Forget about firewalls and VPNs as your security cornerstones. In a world where your employees are logging in from coffee shops and beach resorts, the concept of a security “perimeter” is as outdated as a floppy disk.
When the entire workforce went remote, many companies struggled to scale their VPN infrastructure to meet the new demands.
The Urgent Need for a Holistic Approach To Network Security
The two tectonic shifts, of cloud migration and remote working, have created a security nightmare, demanding a new, holistic approach ro healthcare.
How do you ensure secure network connections for a dispersed workforce? How do you manage access controls without compromising security?
In this evolving landscape, the need for a new security architecture is not just an option; it’s an imperative.
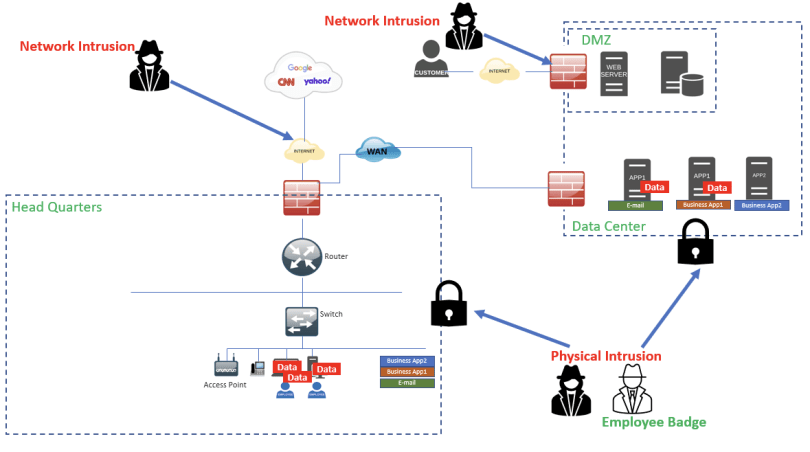
Fig 1: Are you prepared to navigate these complexities, or will you be left behind in the cybersecurity arms race?
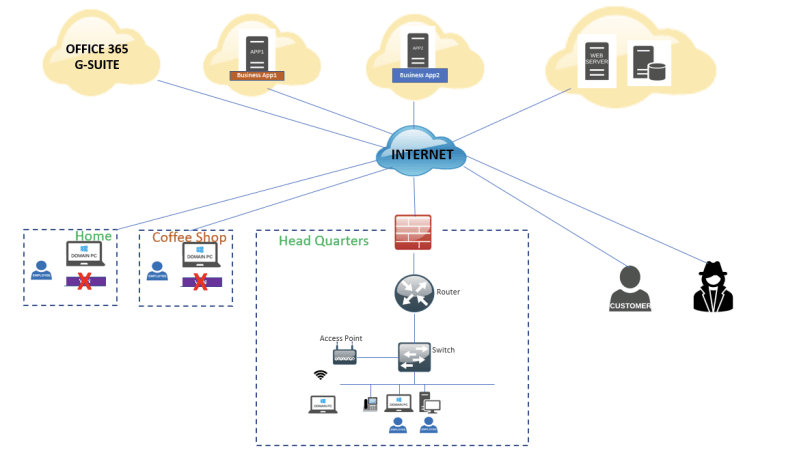
Fig 2: So, what’s the solution to these modern challenges? You guessed it: SASE.
SASE: The Game-Changer You’ve Been Waiting For
How SASE Revolutionizes Security
SASE isn’t just another acronym to add to your cybersecurity lexicon; it’s a transformative architecture designed for the modern landscape of cloud applications and remote workforces.
Forget the notion of a single plug-and-play appliance; SASE is an integrated framework that combines Software-Defined Wide Area Networking (SD-WAN) with a suite of security functions.
SASE includes next-generation firewalls, data-loss protection, Cloud Access Security Brokers (CASB), Secure Web Gateways, and Next-Generation Anti-malware. And the beauty of it? It’s all centralized.
Picture this: A private network within the internet, fortified with all the security functions you need. By connecting all your endpoints to this network, you ensure exclusive, secure access to your cloud applications. This is SASE in action, a unified solution that streamlines security and connectivity.
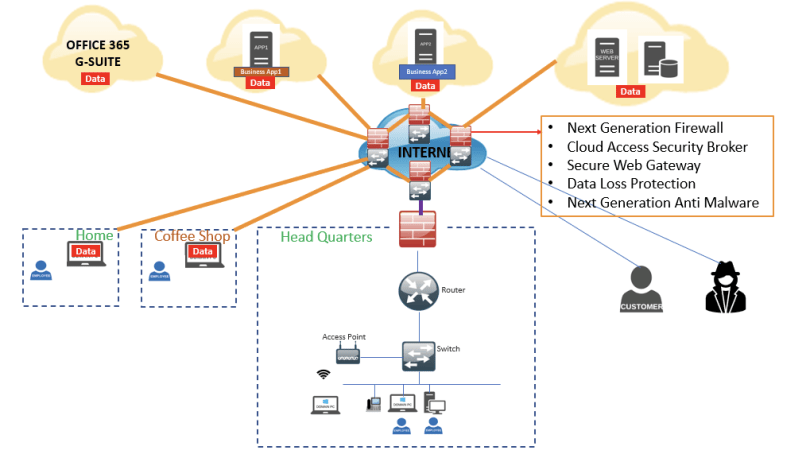
Fig 3: See SASE in Action
The Financial Upside: Why SASE is a Budget-Friendly Choice
No Hardware Costs
Opting for a SASE solution eradicates the need for hardware investments, thereby eliminating associated costs like installation, upgrades, and maintenance. While your physical locations may still require some hardware, these are typically cloud-managed, simplifying the setup process.
Pay for What You Need
SASE is inherently cloud-based, allowing you to tailor your subscription to your specific needs. You pay for the services and bandwidth you actually use, making it a cost-effective choice.
Fig 4: Adjusting these parameters is as simple as tweaking software settings; no hardware modifications required.
Scalability Made Simple
Expanding to a new office location or increasing bandwidth is a breeze with SASE. If you’ve ever managed a cloud-based network, you’ll appreciate the ease with which you can scale your operations.
Centralized Management and Monitoring
Forget the hassle of integrating multiple solutions; SASE offers a unified view, making monitoring and management a streamlined process.
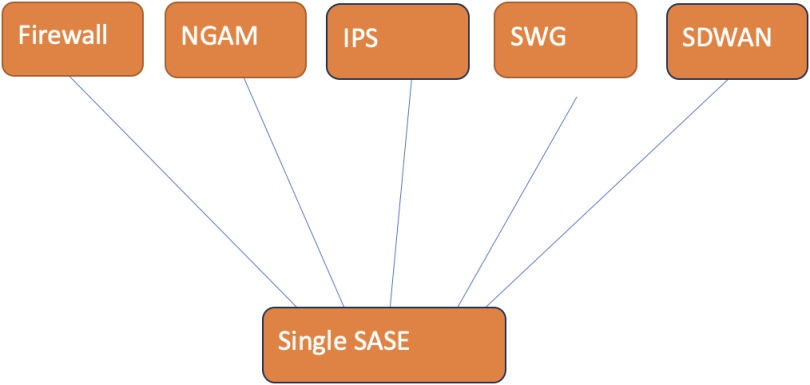
Fig 5: One of the hidden gems of SASE is its centralized management dashboard.
The End of Painful Patching
Consider this: would you rather patch 15 different appliances or just one centralized solution
Traditional patching methods can take up to eight weeks from the time a vulnerability is detected to when it’s finally patched on all hardware. SASE’s cloud-based nature allows for quicker, more efficient patching.
The Bottom Line
Adopting a SASE-based solution could reduce your overall costs by 30 to 40% compared to traditional appliance-based solutions.
So, are you ready to make the switch to a more secure, cost-effective, and scalable solution? Or will you stick with outdated methods that drain your budget and leave you vulnerable? The choice is yours.
The Insider’s Guide To Choosing the Right SASE Vendor
Alright, let’s cut through the noise. The cybersecurity landscape has evolved, and if you’re still relying on traditional security architectures, you’re playing catch-up.
But let’s be clear: not all SASE solutions are created equal. Here’s your roadmap to making an informed decision that aligns with your business needs and budget.
You’ve got vendors knocking on your door, each claiming to be the “next big thing” in SASE. Here’s how to separate the wheat from the chaff.
Types of Vendors in the SASE Space
- Traditional Appliance-Based SASE Vendors: These are the titans of the industry, offering feature-rich solutions. But beware, their cloud strategies often involve merely virtualizing existing appliances.
The result? A solution that’s cumbersome to integrate and manage, and often more expensive for mid-size businesses.
- Cloud-Native SASE Security Vendors: These are the disruptors. Born in the cloud, they’re agile and can easily adapt their offerings to a true SASE model.
If you’ve already invested in their services, it might be wise to extend that relationship into your SASE strategy.
- Ground-Up SASE Vendors: These are the pioneers, building SASE solutions from scratch.
While they may lack the feature maturity of traditional vendors, they offer an architecture that’s purpose-built for SASE. Ideal for mid-size businesses taking their first steps into the SASE world.
- Hybrid SASE Vendors: The systems here occupy a unique position that combines elements of traditional vendors and cloud-native solutions.
Assess Where You Are Now Before You Act
Before diving headfirst into the SASE, it’s crucial to take stock of where you stand.
Your existing security investments, workforce dynamics, and geographic considerations aren’t just variables; they’re the pillars that will shape your SASE strategy.
Here’s your insider guide to making decisions that are not just smart but also financially savvy.
- Leverage Your Current Security Arsenal
If you’ve recently poured capital into a cutting-edge firewall, don’t let that go to waste.SASE is designed to work seamlessly with SD-WAN technologies. So, align your SASE adoption timeline with the expiration of your current SD-WAN contract.
The Takeaway: Maximize ROI to amplify the value of your existing investments while you fortify your security framework.
- Understand Your Workforce Dynamics
Remote work is no longer temporary; it’s become the fabric of modern business.The proportion of your team working remotely isn’t a minor detail—it’s a cornerstone for your SASE vendor selection.
The Takeaway: Customize your vendor selection to accommodate the remote work distribution of your team to ensure a seamless transition.
- Go Beyond Borders
If your business operations span multiple continents, scrutinize the geographic distribution of your potential vendors’ Points of Presence (POPs).The Takeaway: Assess your vendor’s reach if you outsource IT tasks across different regions. The more globally compatible your vendor, the better.
- Pick Quality Over Quantity
Examine POP Metrics. Usually, the higher the number of POPs, the better the connectivity. However, don’t be swayed by numbers alone. Test it.The Takeaway: Ensure each POP is fortified with a robust security stack, offering you not just reach but resilience.
- Prioritize Non-Negotiables
If Data Loss Prevention (DLP) is a regulatory mandate for your business, then your vendor’s DLP capabilities should be nothing short of exceptional.The Takeaway: Focus on mission-critical features: Your vendor selection should be laser-focused and should factor the security features that are indispensable to your operations.
Armed with these insights, are you ready to make a calculated move into the future of security with SASE at your hospital, or clinic?
Your Next Steps For Cybersecurity Excellence
If you’ve made it this far, you’re not just an IT Admin; you’re a strategic decision-maker, poised to elevate your organization’s security posture.
The landscape has shifted, and the old security measures are fading into history. It’s time to adapt or risk being left behind.
Let’s recap the critical takeaways:
- SASE is not a luxury; it’s a necessity. In a world where the perimeter has dissolved, and threats can come from anywhere, SASE offers a unified, agile defense mechanism.
- Vendor selection is crucial. Whether you’re looking at traditional appliance-based vendors or cloud-native solutions, your choice will have long-term implications. Choose wisely.
- Action over theory. This isn’t just about understanding SASE; it’s about implementing it. You now have the insights to make this happen.
Your Roadmap To Get SASE
Why go it alone when you can have a seasoned team of cybersecurity experts guiding you every step of the way? Partner with Consltek Inc, today.

Consltek’s Managed SASE Services are designed to provide you with a tailored solution that fits your unique business needs.
We’re not just vendors; we’re your strategic partners in achieving cybersecurity excellence.
4 pointers to guide your journey with Consltek
- Evaluate your current security infrastructure
- Identify the gaps that SASE can fill
- Select SASE vendors, armed with the right questions and a clear understanding of your needs
- Act fast, because in cybersecurity, complacency is your enemy.
Your call to arms
The future of your organization’s security starts with you, right here, right now. Make your decision count with Consltek before you dive headlong into SASE.
Consult with Consltek. You could end up saving money and getting the best fit solution for your business.





