Cybersecurity is often seen as a technical challenge.
But defending against hostile actors isn’t just the IT department’s or the CISO’s job.
Cybersecurity managers must improve programmes and integrate them into larger strategies.
They must question leaders, hold them accountable, and train everyone.
A well-run cyber programme protects your brand, your data, your customers and gives you a strategic advantage.
In this article we explore
- BCG: The CEO’s Guide to Cybersecurity
- WaTech: Privacy and Cybersecurity Best Practices
- Check Point: Cybersecurity Report 2022
- IBM Security X-Force Threat Intelligence Index 2022 Full Report
- KPMG: Cyber security considerations 2022
- Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches
- Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks, NIST, June 2019
- Guide to Conducting Risk Assessments, NIST
- Ransomware Trends You Need to Know in 2021
- A Global Reset: Cyber Security Predictions 2021
- SolarWinds hack explained: Everything you need to know
Let’s explore this in detail.
#1. BCG: The CEO’s Guide to Cybersecurity

Cybersecurity is typically perceived as a technical issue and daunting.
But defending against hostile actors is not solely the responsibility of the IT department or the CISO.
Those in charge of cybersecurity must strengthen programmes and integrate them into larger strategies.
They must challenge leaders, hold them accountable, and ensure everyone is trained.
A well-run cyber programme not only protects crown jewels but also provides a strategic advantage.
Download: BCG: The CEO’s Guide to Cybersecurity
#2.WaTech: Privacy and Cybersecurity Best Practices
Section 1 analyses existing cyber risks and trends, important findings that suggest opportunities for improvement, and recommendations based on recognised industry best practises for addressing gaps and enhancing the state’s security posture.
Section 2 discussed Privacy. It presents an overview of existing privacy principles and ways to improve adherence, as well as existing privacy frameworks and maturity models.
Section 3 discusses new and existing data sharing agreements. It outlines how agencies can identify data sharing needs, execute and monitor agreements. However, it does not have the force of law and does not constitute legal advice.
Download: #2.WaTech: Privacy and Cybersecurity Best Practices
#3. Check Point: Cybersecurity Report 2022

This report showcases the key attack routes and tactics discovered by Check Point Software researchers over the last year.
From a fresh wave of sophisticated supply chain attacks to the Log4j vulnerability exploit that exposed hundreds of thousands of firms to risk.
This year’s biggest cyber incidents will be reviewed month-by-month before diving into some of the developing patterns that will definitely affect the coming year. Discussing cloud services, mobile and IoT advances as well as the return of Emotet and the Log4J zero-day vulnerability that capped off a busy year.
Download: Check Point: Cybersecurity Report 2022
#4. IBM Security X-Force Threat Intelligence Index 2022 Full Report

IBM evaluated billions of data points from network and endpoint detection devices, IR interactions, domain name tracking, and more to create the IBM Security X-Force Threat Intelligence Index.
This paper summarises data received from January to December 2021.
The insights are available to IBM clients, security researchers, policymakers, the media, and the broader security and business community.
To keep ahead of attackers and protect your vital assets, you need threat intelligence insights more than ever.
Download: IBM Security X-Force Threat Intelligence Index 2022 Full Report
#5. KPMG: Cyber security considerations 2022

From enforcer to influencer in CISO. This period has led firms to reconsider how they engage with and service customers in a digital-first environment.
This shift in attitude to client centricity has accelerated digital transformation, allowing customers to move quickly and safely.
In this dynamic context, cyber professionals shift from enforcers to influencers. The C-suite is aware.
According to KPMG’s 2021 CEO Outlook, a robust cyber strategy is vital to building confidence with key stakeholders (75%).
Defending their partner ecosystem and supply chains is as critical as protecting their own organization’s cyber defences in the context of accelerating digital transformation, according to 79 percent of cyber teams.
Most CEOs (58%) believe they are ready for a cyberattack. Almost every firm now expects some form of cyber event. To minimise the harm, security personnel must be ready to respond, recover, and re-establish trust as rapidly as feasible.
At the same time, they must recognise that risk is fluid in this environment. Controls should be in place to secure the organization’s and clients’ high-value assets, the proverbial ‘crown jewels.’
Over the years, it has been discovered that a lack of preparation and a hasty reaction can be as harmful as the actual incident. Thus, having a plan, practising reactions, and understanding the scope of potential cyber disasters are critical.
Every sector has an opportunity to rethink its reaction and recovery methods and truly shift security left.
Download: KPMG: Cyber security considerations 2022
#6. Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches

The Cybersecurity and Infrastructure Security Agency (CISA) and its partners have responded to numerous ransomware assaults in recent years, including recent attacks on US pipeline and software companies, affecting MSPs and their downstream clients.
Ransomware is a type of software that encrypts files on a device, making them unusable.
Traditionally, criminals demand ransom for decryption. Malicious actors have improved their ransomware strategies over time. Malicious actors increasingly steal data and threaten to sell or disclose it if a ransom is not paid.
These data breaches can cost a firm money and damage client trust.
All enterprises are at danger of ransomware attacks and must protect sensitive and personal data held on their systems. CISA encourages organisations to raise their awareness and follow the suggestions in this report.
Download: Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches
#7. Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks 

IoT is a collection of technologies that interact with the physical world.
Many firms don’t realise how many IoT devices they already use or how they may affect cybersecurity and privacy issues differently than conventional IT equipment.
This guide helps federal agencies and other organisations identify and manage cybersecurity and privacy threats connected with IoT devices throughout their life cycles.
This is the introductory document for a planned series on this topic.
Download: Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks
#8. Guide to Conducting Risk Assessments, NIST
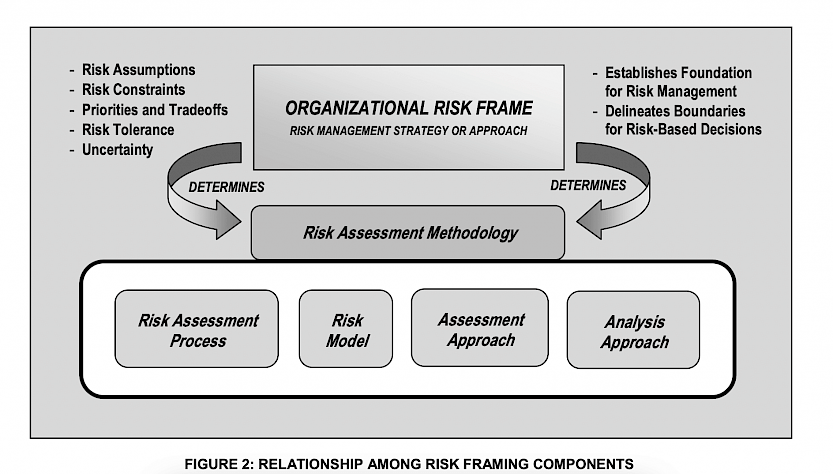
This guide provides a framework for assessing risk.
It is useful for a diverse group of risk management professionals:
- Those with oversight responsibilities for risk management (e.g., agency heads, CEOs, COOs, risk executives)
- Those responsible for organisational missions/business functions (e.g., mission/business owners, information owners/stewards, authorising officials)
- Those responsible for acquiring IT products, services, or information systems (e.g., acquisitors).
Download: Guide to Conducting Risk Assessments, NIST
#9. Ransomware Trends You Need to Know in 2021
Due to the epidemic, the world turned more digital in 2020. This also raised the cyber dangers to businesses.
Ransomware attacks increased 139 percent year-on-year in Q3 2020 compared to Q3 2019.
No industry was spared by ransomware. For example, successful ransomware assaults on schools climbed 388 percent in Q3 2020.
Sadly, these attacks now cripple networks, halt production, and block information flow. These are major incidents.
If corporations don’t pay up, hackers typically exfiltrate data and threaten to publish it elsewhere if they don’t pay up.
These attacks can be extremely costly, with ransom demands ranging from $5 million to $40 million.
For example, Cognizant thinks the April 2020 ransomware assault cost between $50 and $70 million.
Download: Ransomware Trends You Need to Know in 2021
#10. A Global Reset: Cyber Security Predictions 2021

Companies in various industries issue annual forecasts, yet nobody in 2019 predicted the global epidemic or its reaction.
Organizations have to make decisions that affect how they do business permanently. Cyber security guarantees remain despite 2020’s uncertainties.
Threat actors will attack regardless of their targets’ challenges.
These actors are motivated by espionage and money.
This implies firms will continue to be breached, leading in business disruptions, data compromise, reputational injury, and financial loss.
Download: A Global Reset: Cyber Security Predictions 2021
#11. SolarWinds Hack Explained: Everything you need to know
Companies invest millions on cyber-defense to boost growth. Despite that, they struggle to detect and prevent attacks.
As cyberattacks expand in volume and sophistication, there is no one approach to get your defences right.
However, defences must be evaluated regularly, if not continuously.
BreachLock Founder and CEO Seemant Sehgal recently said,
“The problem with cybersecurity is not that we’re not investing enough, it’s that we’re not testing enough to determine whether the defences are functioning.”
Read: SolarWinds Hack Explained: Everything you need to know
Conclusion
Cybersecurity is technical.
It’s not just the IT department or CISO’s role to defend against hostile actors.
Cybersecurity managers must improve and combine programmes.
They must question and train leaders.
A well-run cyber programme protects your brand, data, customers, and strategic advantage.


0 Comments