
Explore how SASE outshines traditional networking with its cloud-native, unified security approach. Discover key differences, benefits, and why it's the…
Most IT partners hand you a roadmap.
We hand you clarity, strategies that scale because they start with your business, not buzzwords.
Security That Solves,
Not Sells
Visibility So Clear, You’ll Wonder How You Managed Without It
Where Business and IT Finally Row in the Same Direction
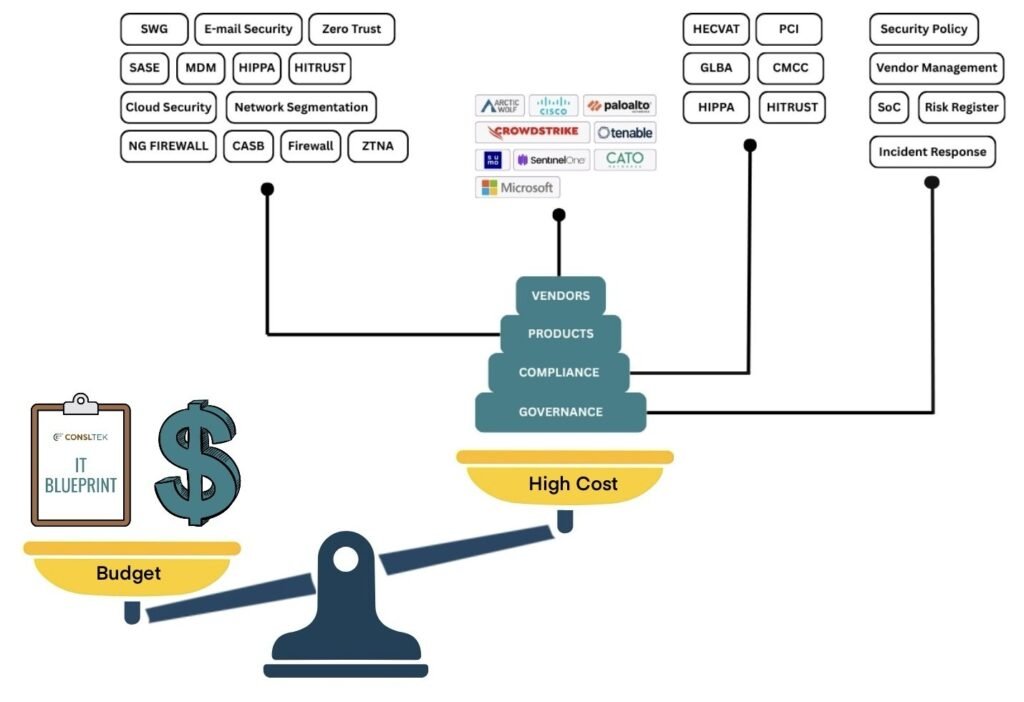
We build a blueprint that ties every dollar of tech spend to what your business actually needs, not what vendors want you to buy.
What You Get (That Others Don’t):
Technology Alignment: Turn IT from a cost center into a growth driver.
Proactive Risk Management: Security and compliance baked in, not bolted on.
Fractional CIO: Big-picture strategy without the big executive price tag.
Security Blueprint
Operations Blueprint
IT Finance Blueprint




Most “free IT audits” end with a pitch. Ours ends with proof.
We don’t sell uncertainty, we remove it.
In just two hours, you’ll see exactly where your IT stands and what’s silently draining your budget.
You’ll walk away with a full diagnostic, posture, gaps, inefficiencies, and wasted spend, with or without us.
No commitments. No fine print.
We guarantee at least $10,000 in savings uncovered, from redundant tools, unused licenses, or forgotten subscriptions.
Because waste hides in plain sight.
Give us two hours. Get your Blueprint. Keep every insight, even if you never work with us again.
No sales push. No agenda. Just answers.
Today’s mid-market doesn’t need more tools, it needs IT that’s secure, strategic, and scalable from day one. Most providers react. We align, translating your goals into tech outcomes that move the needle.
Enterprise-grade performance. Mid-market price. No surprises.
Cyber threats evolve daily. Compliance rules don’t bend. For mid-sized firms, risk isn’t a category, it’s a constant.
We don’t start with fear. We start with trust, delivering always-on cybersecurity and GRC that hardens your foundation before attackers ever reach it.
Fully Managed Cybersecurity (MSSP), 24/7 SOC, Managed Detection & Response (MDR/XDR), and GRC as a Service.
Your IT team is stretched thin, buried in tickets, without time for security or cloud strategy.
We bring financial clarity to chaos, fixed-cost models, transparent reporting, and guaranteed savings.
Within 48 hours, we’ll pinpoint at least $10K in hidden waste, proof that precision pays.
Co-Managed IT, vCIO Strategic Consulting, Technology Roadmapping, Budget Planning.
Mid-market IT budgets shouldn’t feel like roulette. Unplanned costs crush strategy.
We bring financial clarity to chaos, fixed-cost models, transparent reporting, and guaranteed savings.
Within 48 hours, we’ll pinpoint at least $10K in hidden waste, proof that precision pays.
Cost-Effective Pricing, True Fixed-Cost Models, Detailed ROI Reporting.




We don’t just manage IT. We move with you, aligning every process, project, and
person behind your business goals. That’s how strategy turns into results.

Your goals drive every decision we make, not service tiers, not SLAs.
When IT runs in sync with your priorities, roadblocks disappear. Momentum builds. Progress compounds.

Predictability isn’t luck, it’s process.
With ITIL discipline behind every workflow, operations stay steady, even as you scale. Because when your systems run smooth, growth never breaks things.

Issues get solved right the first time, not escalated, not delayed.
Our engineers aren’t learning on your time, they’re applying decades of know-how to deliver results, fast.

You’ll feel it in every interaction, a stable, motivated team that actually enjoys what they do.
That energy doesn’t just stay in Slack threads, it shows up in the quality, speed, and consistency of what you get.

Are you thinking about migrating your on-premise UC solution to cloud? Is your executive management team pushing you on the cloud initiative? Migrating to cloud does makes sense for a lot of business applications.
Migrating on-premises to cloud telephony is a smart decision for a lot of businesses. It brings down management overhead, increases agility and moves expenses from capital expenses to operational expenses.
Migration to EAP-TLS is a major undertaking. This document goes over important questions to ask for a successful migration.

Explore how SASE outshines traditional networking with its cloud-native, unified security approach. Discover key differences, benefits, and why it's the…

Explore the core components of SASE—CASB, FWaaS, SD-WAN, SWG, and ZTNA—and discover how this cloud-native framework revolutionizes network security for…

Discover how Secure Access Service Edge (SASE) is transforming network security for hybrid workforces, enhancing data protection, connectivity, and agility…

Guide to SASE Vendors 2024 In an era where digital transformation is driving businesses to adopt more cloud-based applications, Secure…

Discover how technology enhances compliance management for leaders in all industries, ensuring efficiency and accuracy
After Submitting the form you will get the PDF Download Link !
After Submitting the form you will get the PDF Download Link !
After Submitting the form you will get the PDF Download Link !
After Submitting the form you will get the PDF Download Link !
After Submitting the form you will get the PDF Download Link !
