EAP-PEAP or EAP-TLS?
Download the EAP-TLS Migration Check List.
This is a follow-up to the previous article.
There, we discussed why it is not a good idea to continue using PSK in your business.
When you started your company, it was probably common practice to use WPA2-PSK for your wireless password. Your company grew and you hired more employees. But you still kept using the WPA2-PSK as your wireless authentication mechanism.
In the previous blog why WPA2-PSK is not a good authentication mechanism for wireless.
If you want to tighten wireless security you need to move away for WPA2-PSK. 802.11-2007 standard gives you two options; EAP-PEAP MSCHAPv2 or EAP-TLS.
This blog helps you understand the differences between EAP-PEAP MSCHAPv2 and EAP-TLS.
How secure are these, and the challenges associated with transitioning away from WPA2-PSK.
EAP-PEAP is not secure anymore
EAP-PEAP MSCHAPv2 was introduced as part of the 802.11-2007 security amendment. EAP-PEAP MSCHAPv2 has been (and continues to be) the prominent authentication mechanism.
Over the years, several flaws in the EAP-PEAP MSCHAPV2 protocol have been identified. This makes cracking EAP-PEAP MSCHAPV2 easy. Look up “cracking EAP-PEAP MSCHAPV2” on YouTube. There are numerous videos on how to do it in a short period of time using available tools for free. Even if you use a very long password, you can crack it for less than $20 using online services.
EAP-TLS, uses digital certificates for identity. There is no easy way to break a certificate-based authentication mechanism.
Certificates cannot be shared, but passwords can
A user can share a password with another user to gain access to the wireless network. This can give the user access to the entire company infrastructure. Sharing a password may not be done with evil intent. The fact that it can be shared is a serious flaw in your security protocol.
A certificate issued to a user/device cannot be shared, giving it a different level of protection.
A certificate and its private key can be installed in such a way that the user is unable to export or share it. Unlike a password, a user does not need to know anything about the certificate. A provisioning tool can install it for the user.
No Device Restriction
Users can log in from any device using a username and password. The device could be a compromised one. Furthermore, a user sitting in the parking lot can log into your network or even attempt to break into it.
Only devices that have been provisioned with the certificate can connect to the network when EAP-TLS is used. Any device that has not been provisioned cannot connect to the network. Only devices with valid certificates can connect to the network using certificate-based authentication.
EAP-PEAP is simple to set up
EAP-PEAP is less difficult to implement than EAP-TLS. This is why so many customers continue to use EAP-PEAP for authentication.
EAP-PEAP is easy to put in place. It is very simple to enable EAP-PEAP as your wireless authentication mechanism.
A PKI infrastructure is required to implement EAP-TLS. For most customers, it is a massive undertaking.
A PKI infrastructure must also be properly maintained. Failure of CDP/OSCP components can result in widespread network outages.
Today several vendors offer cloud-based PKI infrastructure. This eliminates the complexity of implementation and maintenance of PKI infrastructure. Some of them are now offering it at an affordable cost and making provisioning much easier.
It is more difficult to distribute certificates than it is to distribute usernames and passwords
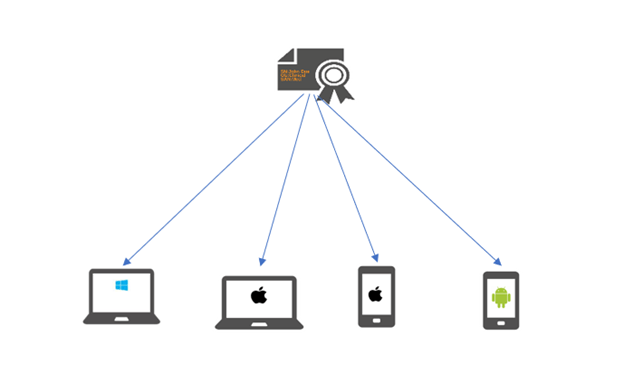
It is simple for an IT administrator to distribute a username and password. Installing a certificate in each device take more effort. It can be difficult to manage many device types and BYOD scenarios. When you add remote workers to the mix, you’re ready to give up on EAP-TLS.
Today, some of the cloud-based PKI solution providers have solutions that will make the transition to EAP-TLS much easier. Everyone will be forced to use EAP-TLS. It is only a matter of time.
EAP-TLS is not supported by all devices
The use of EAP-TLS has grown in recent years. You may still encounter legacy devices that do not support EAP-TLS. Old printers, FAX machines, and cameras as some examples. There workarounds to keep these devices connected to the network without compromising security. Network segmentation is one example. Legacy devices should not be viewed as a major barrier to EAP-TLS adoption.
Summary
From a security standpoint, it is critical to migrate away from WPA2-PSK. EAP-PEAP MSCHAPv2 may appear to be an appealing option. But EAP-PEAP MSCHAPv2 is not secure for today’s world. EAP-TLS may appears to be a bit daunting for a mid-sized business. But EAP-TLS is the right authentication mechanism for wireless. With the right technology partner, you can migrate to EAP-TLS with minimal effort.
If you would like to get a free 30 minute consultation on your migration needs, don’t hesitate to reach out to us.


0 Comments